dropper
脱壳 & 多进程
(1) 脱壳
从github.com/upx/upx上下载最新的源码编译并脱壳即可
(2) 分析无壳程序
main函数:
1 | __int64 sub_7FF6DCB19470() |
sub_7FF6C44D13D4调用了sub_7FF6C44D8860, 可以看到很多LoadLibraryA和GetProcAddress,
用于手动加载Windows API.
1 | FARPROC sub_7FF6C44D8860() |
加载完Windows API后可以看到使用了FindResourceW和WaitForSingleObject,
大概率是将一个程序藏在了.rsrc中然后创建了新进程.
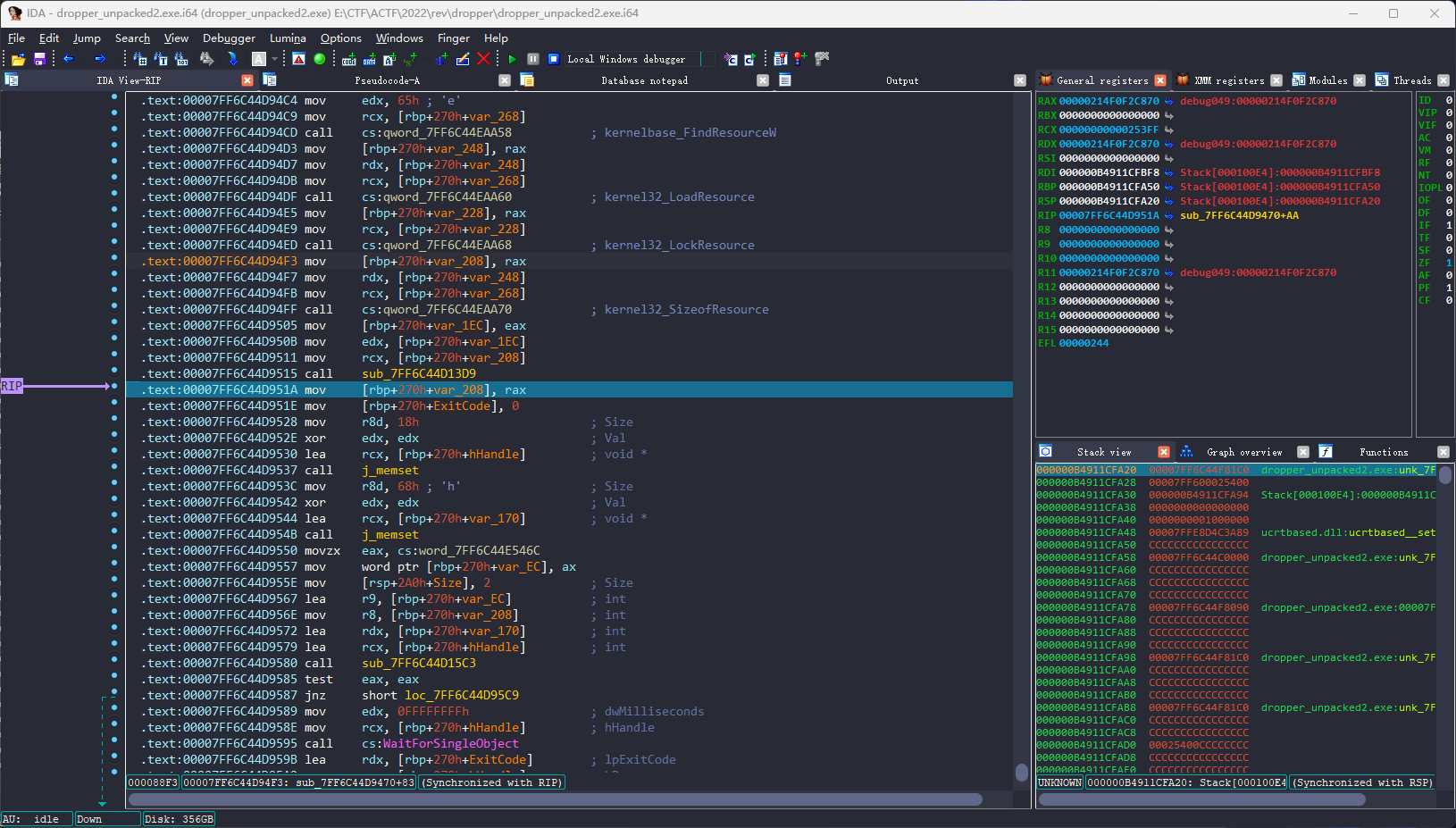
且在sub_7FF6C44D13D9的返回值中发现了MZ头:
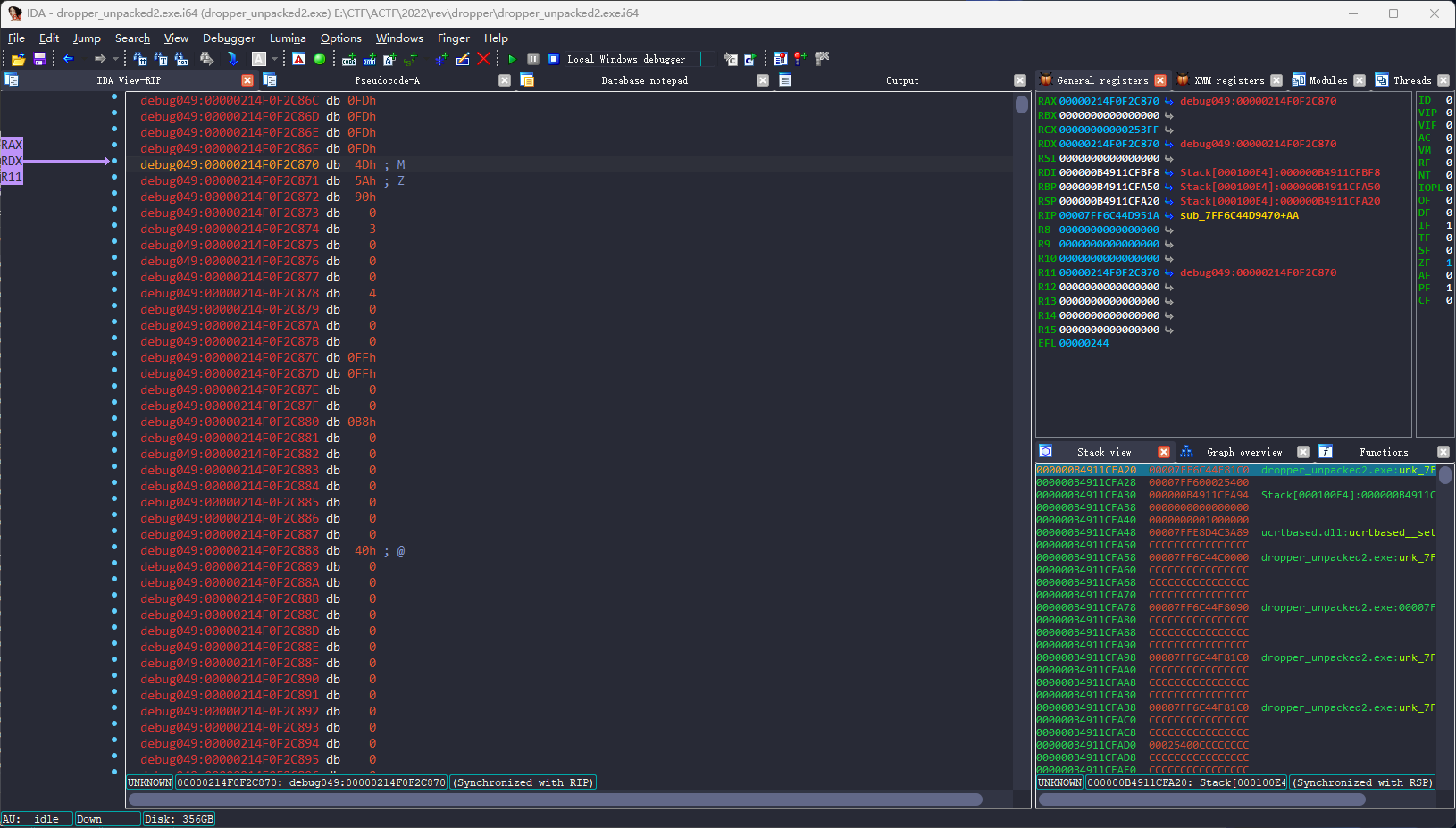
接下来可以使用工具(如Resource Hacker)将.rsrc中的PE文件导出并根据上述sub_7FF6C44D13D9函数,对导出的PE文件进行解码:(假设从资源段导出的文件为dropper_rsrc.exe)
1 | filename = 'dropper_rsrc.exe' |
接下来对dropper_rsrc_real.exe进行分析:
得到真正的程序
main函数:
1 | // sub_00007FF67D14D080 |
程序执行流程总结
(1) 输入字符串
(2) Base64编码 & 10000进制
j_Base64Encode_14001B600函数将输入字符串Base64编码,
随后To128_7FF67D141244函数将Base64编码结果转换为BigInt存储:
1 | // local variable allocation has failed, the output may be wrong! |
To128_7FF67D14BC50也就是相当于:
1 | a1 = 0 |
(3) 对上一步得到的10000进制BigInt进行加法、减法、乘法的操作
在此之前,sub_7FF67D141226会对BigInt类的virtual function table进行更改, 如下图:
左半部分为正常控制流, 但是其中会故意出发除0异常,
异常处理函数让控制流从右侧lea r8, sub_7FF67D14187F的代码块开始执行,
而其中sub_7FF67D14182A会修改vftable, 从而对类对象调用方法进行Hook.
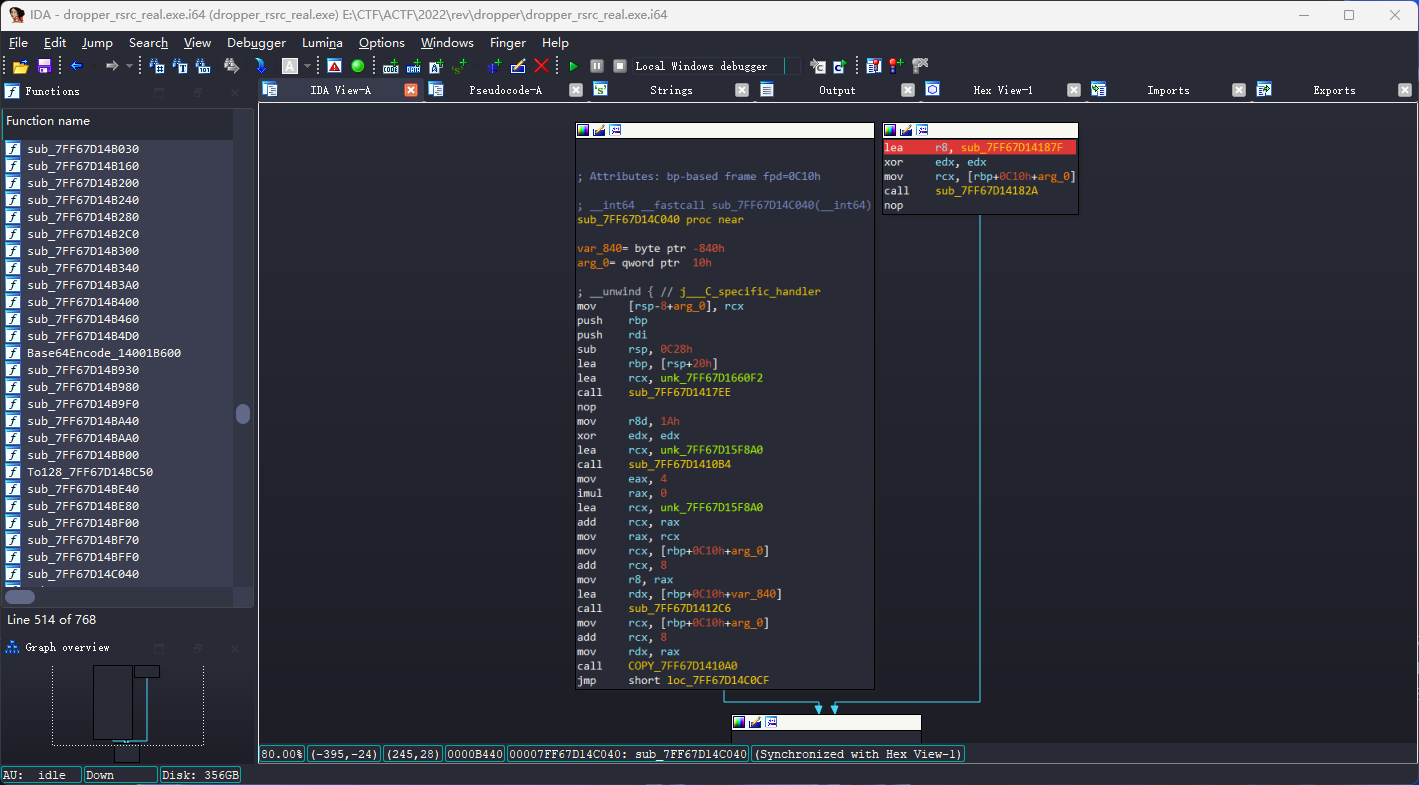
因此, 我们进入sub_7FF67D14187F中, 即可发现加密函数:
1 | __int64 __fastcall sub_7FF67D14C6F0(__int64 a1, __int64 inpStr_a2) |
该函数中依然使用GetObfuString对混淆的字符串进行解密, 解密的结果是许多非常大的十进制数,ToW_7FF67D14110E会将其转换为10000进制: 每四个10进制数字为一组,组合成一个10000进制数字, 每组最小为0000, 最大为9999, 所以可以理解为10000进制.如10进制128转换为10000进制就是0128, 10进制1239999转换为10000进制就是0123_9999.
sub_7FF67D14C6F0调用10000进制的加减乘法, 即ADD、SUB、MUL进行计算,并将结果返回.
(4) 判断最终结果是否为0
调用完sub_7FF67D14C6F0返回到main函数, 还会调用一次SUB_7FF67D14119F,
用来将计算结果与一个固定的数进行剑法操作, 通过动态调试可以发现,固定的数是834572051814337070469744559761199605121805728622619480039894407167152612470842477813941120780374570205930952883661000998715107231695919001238818879944773516507366865633886966330912156402063735306303966193481658066437563587241718036562480496368592194719092339868512773222711600878782903109949779245500098606570248830570792028831133949440164219842871034275938433.
最后sub_7FF67D141014用来判断最终计算结果是否为0.
Script
1 | n = 834572051814337070469744559761199605121805728622619480039894407167152612470842477813941120780374570205930952883661000998715107231695919001238818879944773516507366865633886966330912156402063735306303966193481658066437563587241718036562480496368592194719092339868512773222711600878782903109949779245500098606570248830570792028831133949440164219842871034275938433 |